In our previous post we spoke about the converging forces of cloud native insecurity that are aiming directly at our ‘Digital Superpowers’, and the critical need for a method to ensure that authenticated and authorized humans are in control of the most critical user accounts, resources and powers. We will outline here exactly how that can be accomplished.
In our last blog, we talked about how truly credential-free authentication is the last critical step to eliminating breaches caused by:
But this still only solves part of the problem. The true root of the vulnerability goes much deeper than just passwords. It is the Chain of Trust that ultimately links back to and relies upon centralized, cloud based user ID directories and certificate authorities for authentication and authorization of devices. Every one of those stops along the Chain of Trust are a point of vulnerability.
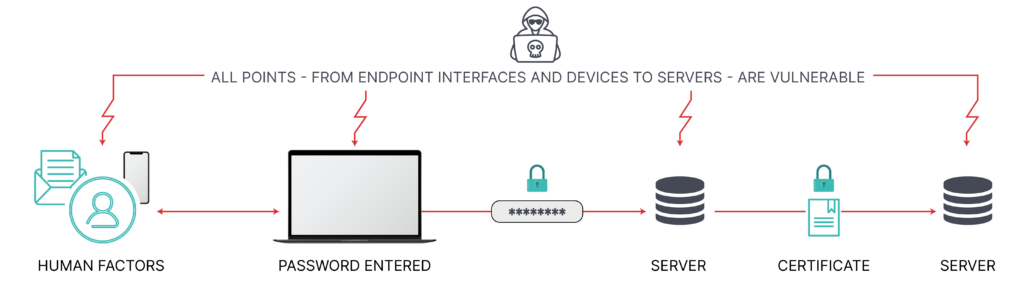
As with encryption of data, we must eliminate the role of centralized, cloud-based databases and servers in granting access permissions. And it’s not impossible. But it does require a leap of imagination.
Restriction of access control - to both data, application and device functions - can be accomplished cryptographically, with unbreakable AES 256 keys generated on end user devices in a decentralized, peer-to-peer process.
For both of these critical vulnerabilities, by decentralizing, we reduce the attack surface to something much more manageable: a device controlled by a human end user.
In Step 1, we took the Cloud off the table as a vector for attack. Attackers will then of course focus on the end point devices, where keys for data and access control are now stored. End users are notoriously fallible and, when connected, their devices are prone to attack. So what do we do about that?
Active defenses involving cloud-based monitoring and endpoint software, are an important piece of the puzzle, but as noted above we are in an arms race there, hoping to stay one step ahead of attackers. These approaches are efficient and effective for many, or most day-in and day-out use cases, but we must assume that when the target is valuable enough they can and will be defeated. Further, the Internet of Things, Bionics and AI pose an even more fundamental question: who or what will control them?
A core principle for cybersecurity - and cyber architecture generally - therefore must be to have an element of Humanization that is automated in the workflows.
While this may sound impractical, it is actually quite feasible with Step 3.
These are the key steps.
None of these steps are in themselves new. The difference is in how they are integrated into a unified workflow in a new architecture, that addresses the vulnerabilities of the Cloud while preserving its efficiency. The architecture’s foundation is a logical construct called a Circle: a private network of devices formed by encryption - the possession of a unique AES 256 key - without the need for VPN or Firewalls.
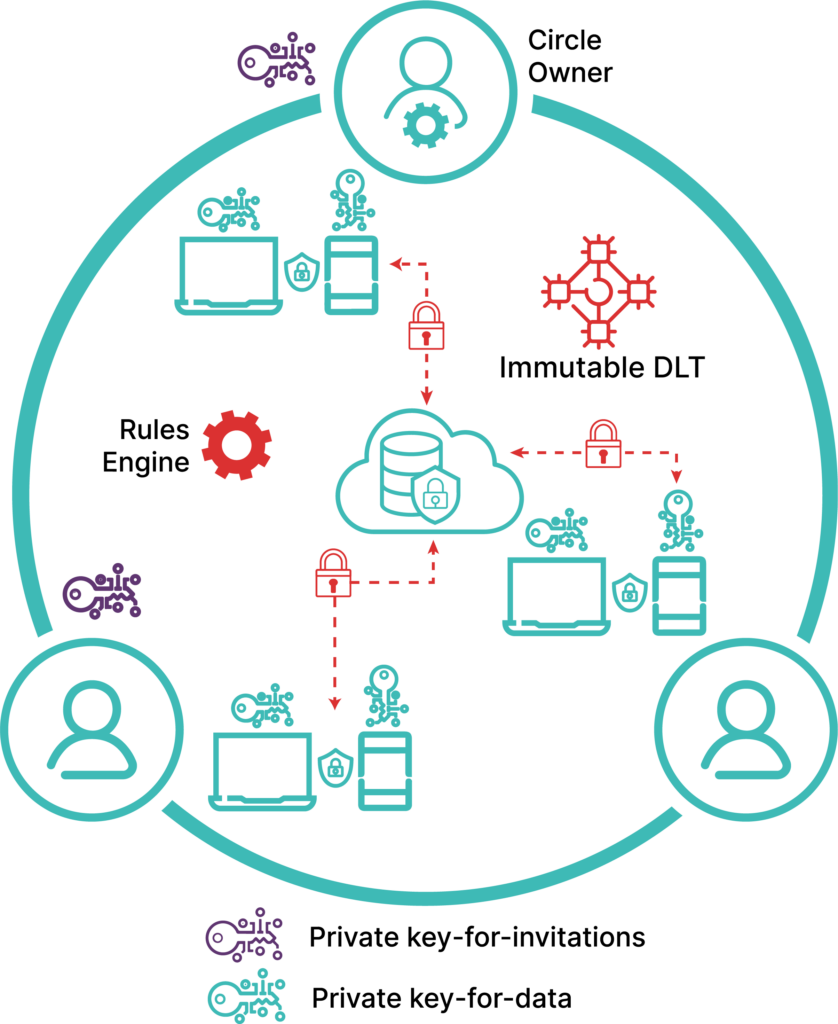
In this architecture, there is nothing in the Cloud to attack. An attacker can penetrate - and even “own” a device - but cannot gain access to any truly important data or functions without completing a human-in-the-loop identity verification with other devices and the human users that control them. The architecture is also flexible: any level of steps and rules for verification and authentication can be defined:
We believe that, at the highest levels of configuration, this is impervious to external attack. To defeat it, the attacker must penetrate a small group of humans that know each other in this “Circle-of-Trust.”
Human-in-the-loop identity verification + authentication provides a powerful new optional step up authentication for permitting actions, events, and data access when needed. And the key is that it accomplishes this with far less friction than current methods that are widely used.
Most thinking and solutions in cybersecurity today are focused on the fallibility of humans as the most common source of breaches and breakdowns. We don’t deny that to be true. Where we differ is in having blind faith in machines and software alone to solve all of our vulnerabilities. The stakes are simply too high, with converging forces that put ever more power and risk into the hands of these tools. We need to rethink our approach and put humans back in the loop of control and verification when it really matters but doing it in a way that minimizes friction and supports the distributed, hyper-connected world we now live in.
What we have outlined here is more than a theory. It is an architecture that we have implemented into a platform and are now making available to developers as a REST API.
At Circle we are reimagining cybersecurity and have developed a revolutionary, breakthrough architecture based on the principles articulated above to address the weaknesses of current approaches, while preserving the benefits of the cloud.
If you want to radically improve the identity and data security of your systems and applications, we welcome you to join our Early Access Program. As an API play, we made it easy and seamless for you to embody the above principles in your security architectures with little or no code.
